Data Governance and Privacy
1.1 WHAT IS DATA GOVERNANCE
Data Governance is a framework for data management that assures the Availability, Applicability, Integrity, and Security of data. This framework is a set of processes that help to ensure that the important, sensitive, and critical data is well-managed, protected, and meets the precise standards and business rules. Stakeholders use these processes in getting benefits from different technologies. In other words, Data Governance is streamlined coordination of people, processes, and technology which acts as a bridge between business and IT for decisions and initiatives. People, processes, and technologies are at the core of good Data Governance. However, technology only serves as an enabler and not as an essential element for Data Governance.
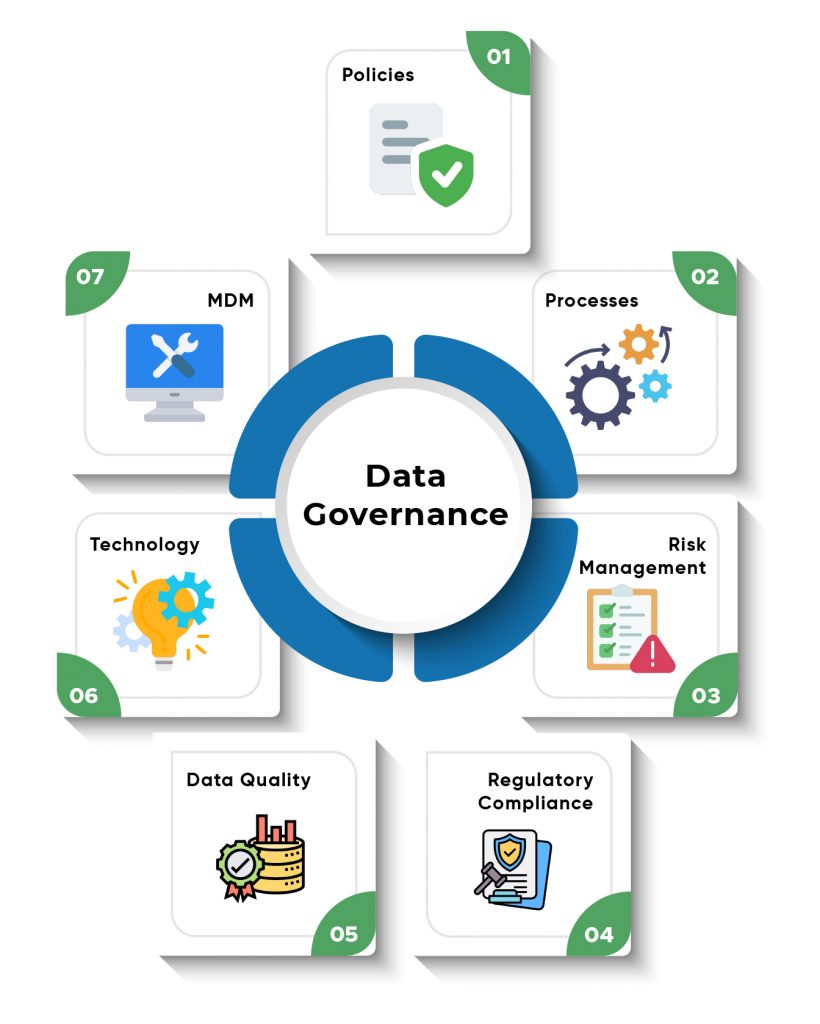
1.2 KTM’S APPROACH OF SETTING UP A DATA GOVERNANCE STRUCTURE
We, at Kualitatem, have consultants with decades of experience in streamlining and documenting business processes. Our consultants have devised a thorough methodology to automate business processes. This is because of their hands-on experience in different business verticals. Our knowledge-base that covers more than 10 years also helps us greatly in this regard.
1.2.1 DEFINE STRATEGY
First and foremost, Kualitatem, with the help of key stakeholders, defines a strategy to set up the Data Governance structure. Following this, we document a mission statement and explain the overall goals of the program. We then choose a data model for the Data Governance structure to explain who has the authority to use this data. Once done, we take a sign off from the client-side executives.
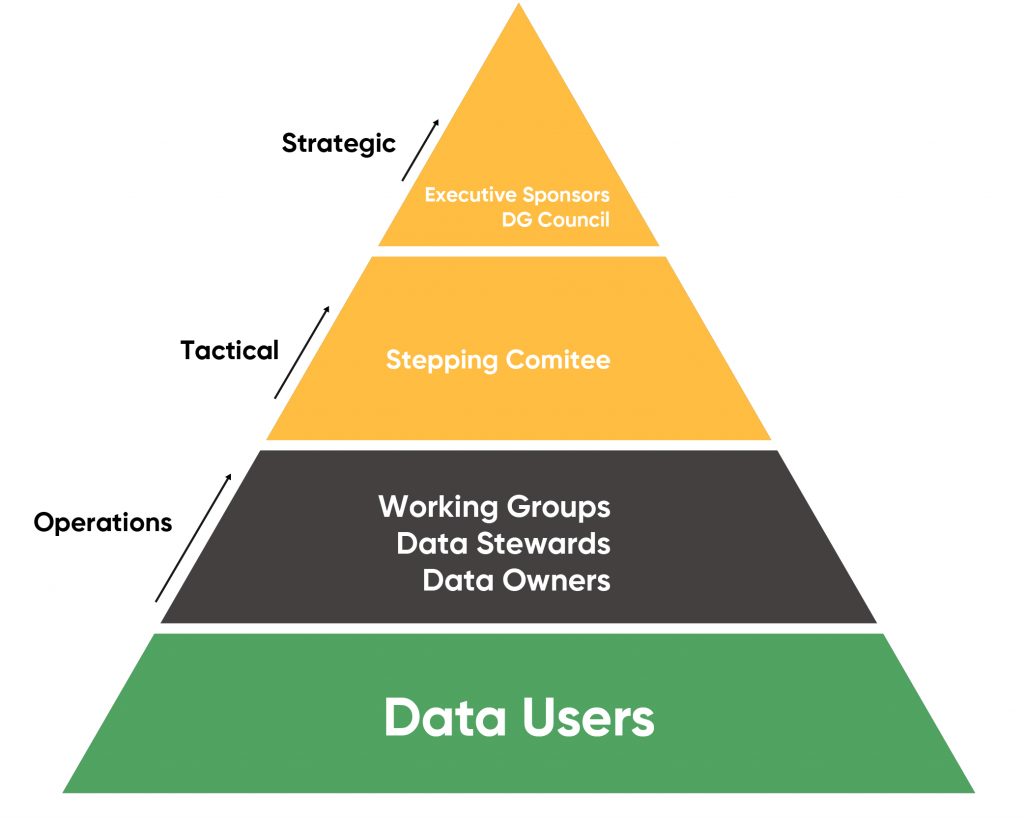
1.2.2 SELECT A DATA GOVERNANCE MODEL FOR TEAM
We adopt a 4-tiered approach for the Data Governance Model.
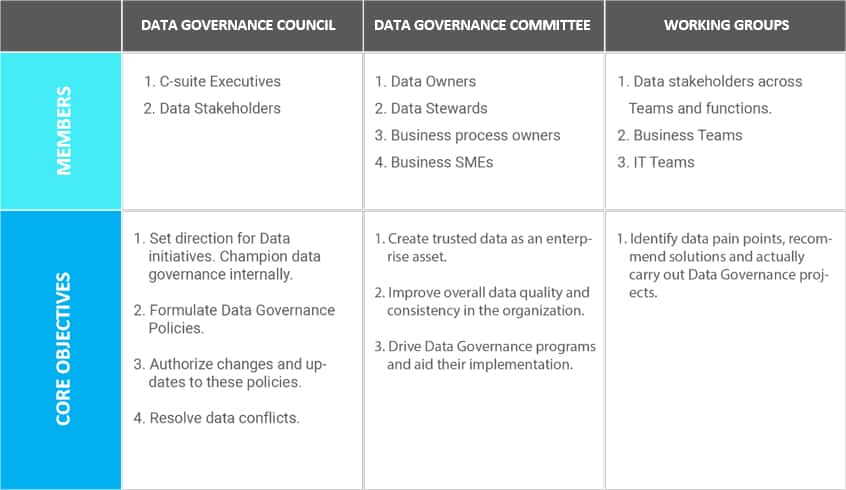
- Data Governance Council (DGC): It is the apex body that internally champions data governance and drives awareness and transformation within the organization. It is also the final decision authority in case of unresolved data conflicts.
- A group of senior-level executives (“Steering Committee”): At the tactical level lies the Steering Committee, a cross-functional body that acts as the interface between the DGC and the working groups. This committee makes high-level decisions and is responsible for most of the on-ground implementation of data governance principles.
- Work Groups: Working groups are cross-functional teams that identify data-related pain points and devise collaborative solutions. They also implement these solutions. Working groups consist of data owners, data stewards, and data users. They are accountable, champion data governance, and use organizational data to carry out their business roles. Of these, data stewards are of particular interest.
- Data Governance Office / Master Data Council: This group offers guidance and work with all business units and IT so that data governance and strategies remain common throughout the organization. This group establishes success metrics. This group also monitors and reports data quality and data governance metrics.
- Data Governance Working Group: The working group (“Data Governance Working Group”) carries out much of the administrative work. This group drives the data management and data quality for specific subject areas. This group also has the subject matter expertise for both business and IT issues.
1.2.3 ENDORSE AND DEVELOP POLICY AND PROCEDURE
We develop the roles, policies, procedures, and practices for data management after defining them, to improve the data quality and avoid the associated costs of bad data. Following this, we set up a data quality team (part of “Data Governance Working Group”) tied to executive level sponsorship. This team is responsible for the creation of enforceable policies, procedures, and standards that aid in enhancing enterprise-wide data quality.
We document these policies, after getting approval from the “Steering Committee”, and communicate them to all the stakeholders. These policies have metrics to show how adherence to these policies can make a significant impact on the business.
1.2.4 ESTABLISH A BUSINESS TEAM
We set up a skilled business team as Data governance needs both business and IT experts. Our business communicates the business needs in relation to the data. We explain how we collect data and how our decision-makers use it, such as C-level management.
Our skilled business team is also responsible for understanding how poor data enters a system. They also develop ways to remediate problems. They are the authority to make changes to poor data at the enterprise and departmental levels.
1.2.5 ESTABLISH AN IT TEAM
We establish an IT team responsible to provide tools for the people on the business team to work with the data. They are also responsible for providing support to the applications that are used by the company’s data. The key rule here is to keep the toolset as minimum as possible.
While the established business team handles policy development, the IT team handles the actual data compliance and security features. IT also provides metrics to help business experts in evaluating data quality and policy adherence. They also determine if any changes need to be made.
DATA PRIVACY
“Data Privacy” also referred to as “Information Privacy” is the feature of information technology that deals with the ability of an organization or an individual to determine which data from the system could/should be shared with the outside parties.
For Data Privacy, each law or compliance regulation responds to the needs of a particular industry or section of the population.
- Children’s Online Privacy Protection Act (COPPA) – gives parents control over what information websites collect from their kids.
- Health Insurance Portability and Accountability Act (HIPAA) – ensures patient confidentiality for all healthcare-related data.
- Electronic Communications Privacy Act (ECPA) – extends government restrictions on wiretaps to include transmissions of electronic data.
- Video Privacy Protection Act – prevents wrongful disclosure of an individual’s personally identifiable information stemming from their purchase of audiovisual material.
- Gramm-Leach-Bliley Act – mandates how financial institutions must deal with the private information of individuals.
2.1 KTM’s DATA PRIVACY SERVICES
Kualitatem Data Privacy services enable organizations to address the following three objectives in a unified and cross-disciplinary way.
- Traditional IT security approaches that focus on protecting the organization’s IT infrastructure. We do this by securing the network edge and end points that require augmentation with protective measures. These measures focus specifically on protecting the data that is stored and moved through the infrastructure.
- Privacy-related protective measures must extend beyond those aspects of privacy that overlap with security. We do this to include protective measures that focus on capturing, preserving, and enforcing the choices customers have made. This is with respect to how and when third parties may collect, process, use, and potentially share their information.
- Data security and data privacy compliance obligations must be rationalized. They must be addressed through a unified set of control objectives and control activities that meet the requirements.We adopt Microsoft’s Data Governance for Privacy, Confidentiality, and Compliance (DGPC) framework to ensure data privacy at the client end. The DGPC framework, as mentioned above, is organized around three core capability areas: people, process, and technology.
2.1.1 PEOPLE
Data privacy processes and tools are only as effective as the people who use and manage them. An important first step that we take is to establish a DGPC team that consists of individuals from within the organization and give them clearly defined roles and responsibilities, adequate resources to perform their required duties, and clear guidance on the overall data governance objectives. See table “Key Teams in Data Governance Structure” above. Essentially, this is a virtual organization whose members are collectively responsible for defining principles, policies, and procedures that govern key aspects of data classification, protection, use, and management. These individuals—commonly known as “data stewards”—also typically develop the organization’s access control profiles, determine what constitutes a policy-compliant use of data, establish data breach notification procedures and escalation paths, and oversee other related data management areas.
2.1.2 PROCESS
With the right people involved in the DGPC effort, we focus on defining the processes involved. We do this by examining various authority documents (statutes, regulations, standards, and company policies and strategy documents) that spell out the requirements that must be met. Understanding how these legal mandates, organizational policies, and strategic objectives intersect, we help organizations consolidate their business and compliance data requirements (including data quality metrics and business rules) into a harmonized set.
2.1.3 TECHNOLOGY
Our approach involves filling out a form called the “Risk/ Gap Analysis Matrix”, which is built around three elements:
2.1.3.1 THE INFORMATION LIFE CYCLE
Firstly, understand how the information flows throughout the system and how we access and process the information at various stages. Understanding the risks within each life-cycle stage helps clarify what safeguards we require to mitigate those risks.
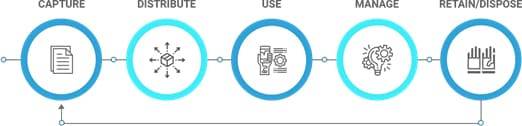
An important node in the above information life cycle that normally gets overlooked, as we did in the diagram, is transferring or sharing the information/data.
A new information life cycle begins when a user copies or removes data from storage as part of a transfer. Here, we check the security and privacy of the data that the user transfers. We check for the transfer medium and the associated risks e.g. private networks, the internet, and storage media sent by courier. For example, if the user shares media by courier or postal mail then their data can be lost or stolen. Therefore, they should take measures such as encryption to protect the data on the media that they share. Data security also requires an understanding of how the recipient organization’s policies, systems, and practices differ from those of the current keepers of the data. If the recipient does not have the same security capabilities and processes as the current keepers of the data, protections may need to be placed on the data or the process before transfer.
2.1.3.2 TECHNOLOGY DOMAINS
In addition to checking the information life cycle, we also systematically evaluate whether the client’s technologies that protect their data confidentiality, integrity, and availability are sufficient to reduce the risk to acceptable levels. The following technology domains provide a frame of reference for this task:
- Secure infrastructure—To safeguarding confidential information we understand the requirement of a technology infrastructure that protects computers, storage devices, operating systems, applications, and the network against malicious software, hacker intrusions, and rogue insiders.
- Identity and access control—Identity and access management (IAM or IdM) technologies help protect personal information from unauthorized access while facilitating its availability to legitimate users. These technologies include authentication mechanisms, data, and resource access controls, provisioning systems, and user account management. From a compliance perspective, IAM capabilities enable clients to accurately track and enforce user permissions across the enterprise.
- Information protection—Confidential data requires persistent protection as users share them within and across organizations. We make sure that the client’s databases, document management systems, file servers, and practices correctly classify and safeguard confidential data throughout the life cycle.
- Auditing and reporting—Technologies for systems management, monitoring, and automation of compliance controls are useful for verifying that system and data access controls are operating effectively, and are useful for identifying suspicious or noncompliant activity.
2.1.3.3 DATA PRIVACY AND CONFIDENTIALITY PRINCIPLES
In addition to checking the information life cycle, we also systematically evaluate whether the client’s technologies that protect their data confidentiality, integrity, and availability are sufficient to reduce risk to acceptable levels. The following technology domains provide a frame of reference for this task:
The following four principles help the clients in selecting technologies and activities that protect their confidential data assets. They are high-level principals that one can easily convert into more detailed principles after getting details about the environment and technology stack.
- Principle 1: Honor policies throughout the confidential data life span. This includes a commitment to process all data in accordance with applicable statutes and regulations, preserve privacy, respect customer choice, consent, and allow individuals to review and correct their information, if necessary.
- Principle 2: Minimize the risk of unauthorized access or misuse of confidential data. The information management system should provide reasonable administrative, technical, and physical safeguards to ensure confidentiality, integrity, and availability of data.
- Principle 3: Minimize the impact of confidential data loss. Information protection systems should provide reasonable safeguards such as encryption, to ensure the confidentiality of data that is lost or stolen. Appropriate data breach response plans and escalation paths should be in place, and all employees who are likely to be involved in breach response should receive training.
- Principle 4: Document applicable controls and demonstrate their effectiveness. To help ensure accountability, the organization’s adherence to data privacy and confidentiality principles should be verified through appropriate monitoring, auditing, and use of controls. Also, the organization should have a process for reporting noncompliance and a clearly defined escalation path.
DELIVERABLES
| DELIVERABLES | DESCRIPTION |
|---|---|
| DATA POLICIES | Data policies are a collection of statements that describe the rules that control the integrity, security, quality, and use of data during its lifecycle and state change. |
| DATA STANDARDS | While data policies guide what to do and what not to do with regards to data, data standards are more detailed rules on how to do this. Sample data standards include naming standards, data modeling standards, and other data architecture standards. |
| RESPONSIBILITY MATRIX | Data Governance Responsibility Matrix explains who has the authority to do what with data and who is responsible for what activities. |
| RESOLVED ISSUES | Data governance controls the procedures of addressing data related issues including data quality issues, data naming, business rules conflicts, data security issues, and service level problems. |
| DATA MANAGEMENT SERVICES | Data governance function coordinates data management projects and service development efforts across the organization. As a result, it drives better data management projects to have a higher success rate, deliver more value, reduce time to deliver, and cost to implement. |
| QUALITY DATA & INFORMATION | An obvious outcome of data governance is data with improved quality, easier access, managed, and auditable security. Quality data and information, as a result, is the core deliverable of the data governance function. |
| RECOGNIZED DATA VALUE | One of the information architecture principles is to treat data as an asset. A key output of data governance is to evaluate core enterprise data assets – what business processes they support? How critical are these processes? How critical are these data elements in support of these processes? What are the ramifications and risks to the organization if they are unavailable or incorrect? |
