Top 10 Pen Testing Tools For 2021
- August 12, 2021
- maira
Why organizations remain vulnerable to cyber security threats
Penetration tests and vulnerability assessments are high in demand due to continuous breaches we see every day. Last year’s SolarWinds breach brought governments and corporate entities on high alert, and for good reason.
Organizations are vulnerable to a range of different things: from phishing attacks, to inadequate network parameters and endpoint security, highly developed ransomware attacks, to name a few.
On a regular basis, the most common threats that organizations have to deal with are the following:
- Checking an organization’s defenses
- Determining what protections need to be implemented to improve defense effectiveness
- Regulatory compliance (some cyber-security laws require period penetration tests to be conducted)
- Security assessment i.e., discovering flaws and bugs in a company’s cyber defense
Their vulnerability often comes as a result of a lack of security awareness, unclear data security practices, an absence of training for employees, and a range of other reasons.
Adopting a security awareness maturity model helps companies cultivate a four-step path to building a strong security model defense and identifying why their current
Broadly speaking, penetration can happen in 4 different ways:

The types of tools you’ll need to conduct a good pen-test
The tools that a penetration tester requires depends on the type of pen test being conducted. As a company that offers security testing services, these are the types of pen-test tools we often employ in various situations:
– Vulnerability scanners
Scans environments for bugs and configuration errors, and helps penetration tester identify any possible vulnerability for initial penetration of the environment.
– Network sniffers
Gathers and analyzes network traffic, enabling a pen tester to detect active programs, passwords, or confidential data on a network stream.
– Password crackers
A program that attempts to recover passwords that are stored or shared in an insecure form.
– Web proxies
Captures and changes communication between the browser and webserver of an enterprise. Aims to identify and exploit HTML vulnerabilities in order to then launch attacks.
– Port scanners
Detects open ports on a server, which provide information about applications and operating systems (OS) with network access in order to identify potential attack vectors.
The tools
Nessus
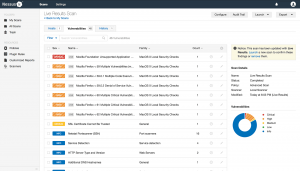
Provided by Tenable under a range of licensing styles, Nessus is the most common vulnerability scanner owing to its large library of vulnerability signatures. A Nessus scan will look over the target system, locate any operating utilities, and include a list of vulnerabilities discovered, alongside updated data for manipulation and restoration. These scans include a list of possible attack vectors for obtaining access to a target network or device to a penetration tester.
Top features:
- Large template library with 450+ templates
- Has advanced scanning features with enable scans to be tailored as needed
- Customizable templates
- Can scan for specific vulnerabilities
Supported platforms: Linux, Fedora, Mac OS X, Ubuntu, among others.
Burp Suite
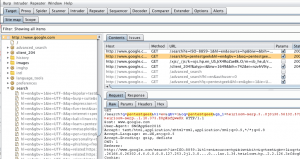
Portswigger’s Burp Suite is a series of device security research techniques. Burp Proxy, their web proxy, is perhaps the most well-known of these applications. Burp Proxy can be used to conduct a man-in-the-middle (MitM) attack by sitting between a web server and a browser (either their own or someone else’s).
Top features:
- Scanning features: enables easy scan set-up; recurring, scheduled, and agent-led scanning, custom and out-of-the-box configurations, multi-faceted ASTs etc.
- Integration features: Can be integrated with all major CI/CD platforms, has an API-driven workflow, role-based access control,
Supported platforms: Windows, Linus, and Mac OS X
Nmap
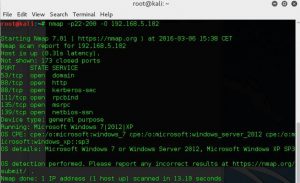
The Network Mapper (Nmap) is a software that helps you analyze a network or system. Nmap comes with a wealth of built-in information in the form of a wide range of scan modes. These various forms of scans are intended to circumvent protections or detect peculiar characteristics that can be used to distinguish certain operating systems or applications.
Top features:
- Strikes a balance between accessibility and extensibility
- Experienced users can fine-tune their network search
- Live report on scan progress
Supported platforms: Most operating systems are supported, including Linux, Microsoft Windows, FreeBSD, OpenBSD, Solaris, IRIX, Mac OS X, HP-UX, NetBSD, Sun OS, Amiga, and more.
Wireshark
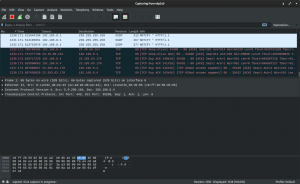
Wireshark is by far the fastest network sniffing platform online. It’s the de-facto standard across many commercial and non-profit enterprises, government agencies, and educational institutions. Thanks to its wide number of integrated protocol dissectors, it’s able to define and break down network traffic coherently.
Top features:
- Deep inspection of hundreds of protocols, with more being added all the time
- Live capture and offline analysis
- Live data can be read from Ethernet, IEEE 802.11, PPP/HDLC, ATM, Bluetooth, USB, Token Ring, Frame Relay, FDDI, and others (depending on your platform)
- Offer decryption support for many protocols
Supported platforms: Runs on Windows, Linux, macOS, Solaris, FreeBSD, NetBSD, and many others.
John the Ripper
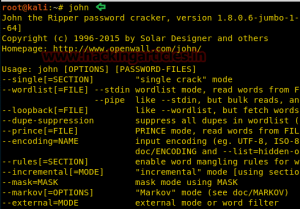
The password breaking tool John the Ripper is well-known and commonly used. It is mainly intended for use on CPUs, but GPUs are supported for faster cracking.
Top features:
- Large library of compatible hash formats
- Supports most cracking strategies
- Versatile and customizable
Supported platforms: Unix, macOS, Windows, DOS, BeOS, and OpenVMS.
SQL Map
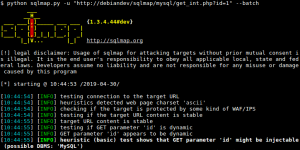
sqlmap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester and a broad range of switches lasting from database fingerprinting, over data fetching from the database, to accessing the underlying file system and executing commands on the operating system via out-of-band connections.
Top features:
- Can automatically detect and use the SQL injection vulnerability database and the access server
- Has a powerful detection engine
- Has a penetration tester variety of characteristics, accesses to the underlying file system to extract the fingerprint database connection and execute commands that take away
Aircrack-ng

Aircrack-ng is a network security pen testing tool that comes with a series of utilities to assess Wi-Fi networks for possible vulnerabilities. It provides critical operations of monitoring, testing, attacking, and cracking.
Top features:
- Capture data packets and export the data to text files for processing by third party tools
- Carry out replay attacks, de-authentication attacks
- Creates fake access points
- Checks Wi-Fi cards and driver capabilities
- Can be used to crack WEP and WPA (1 and 2)
Supported platforms: Linus,Windows, MacOS, FreeBSD, OpenBSD, NetBSD, Solar, eComStation 2.
Metasploit
Metasploit is a penetration testing framework popularly used by both cyber attackers and ethical hackers. The Metasploit Project has two versions – the open-source sub-project Metasploit Framework and licensed version Metasploit Pro.
Top features:
- Exploit code and payloads that can be developed and executed against a remote target machine
- Provides command line interface to work on
Supported platforms: Windows, Linux, Ubuntu, Red Hat
Netsparker
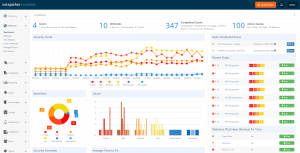
Netsparker is an automated, yet fully configurable, web application security scanner that enables you to scan websites, web applications and web services, and identify security flaws. Netsparker can scan all types of web applications, regardless of the platform or the language with which they are built.
Top features:
- Use advanced local crawling and scanning features
- Automate and integrate manual testing in proxy mode
- Centralized vulnerability management and visibility
Supported platforms: Windows 7, Web browser (OS agnostic), Windows 8, Windows 10
Acunetix
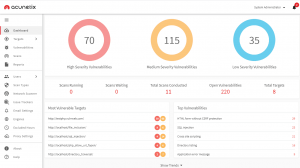
In general, Acunetix scans any website or web application that is accessible via a web browser and uses the HTTP/HTTPS protocol.
Top features:
- Offers a strong and unique solution for analyzing off-the-shelf and custom web applications including those utilizing JavaScript, AJAX and Web 2.0 web applications.
- Has an advanced crawler that can find almost any file
Supported platforms: Windows, Linux, MacOS (Catalina and Big Sur), Ubuntu
While some say that the best pen-testing tool is as good as the tester using it, we hope these pen testing tools make it easier for you to detect vulnerabilities, and simulate cyber-attacks.
If your business has a mobile app and/or a website, then we highly recommended hiring a reliable penetration security testing services partner. It will resolve any malicious elements of your digital business and mitigate hacker threats.