6 Essential Guidelines For Mobile App Developers

- September 23, 2015
- admin
As the mobile apps grow exponentially, the security and privacy of individual users is also at stake. Mobile industry, gadgets and Internet of Things are penetrating into consumers’ lifestyles and since most of the users are non techie so they are highly vulnerable to the threats of technology adaptation.
This security gap demands high investments in this field both in the form of solutions as well as development’s best practices.
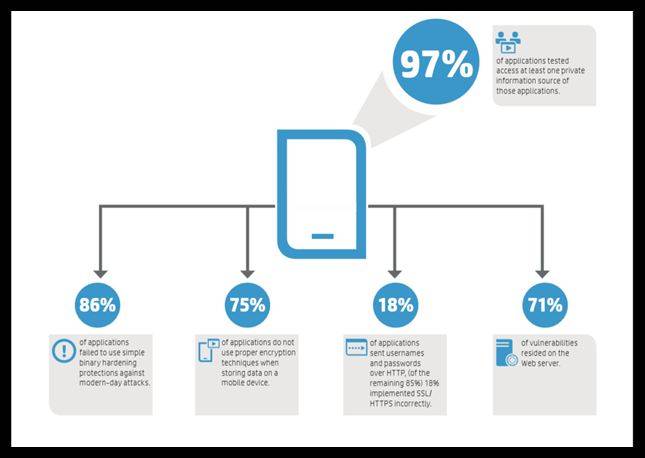
Hp launched a research report of about 2000 mobile apps from 600+ different companies. Key finding of the report are:
- 97% of applications tested could access at least one private information source
- 86% of applications failed to use simple protections against modern-day attacks
- 75% of applications do not use proper encryption techniques when storing data on a mobile device
- 18% of applications sent usernames and passwords over HTTP, while another 18% implemented SSL/HTTPS incorrectly
© Copyright 2014 Hewlett-Packard Development Company, L.P.
In order to keep the mobile apps safe and secured from different security threats, the developers should follow the following guidelines while developing the applications:
- Code Injection and XSS Attack:
A mobile app using HTML5 faces Code injection attack. As web technology allows data and code to be executed at the same time. Unfortunately, if developers are not careful while developing mobile apps, untrusted data-code combination can be triggered and injected. XSS attacks work in the same way in which JavaScript code is inserted into data fields. Besides, mobile browser access the application cookies and hence can hijack the session.
Counter For Code Injection and XSS Attacks:
Application hardening can be effective in code injection attacks in which the surface area of the app is reduced for the vulnerability. Besides, Run Time protection also secures the apps. Both can be achieved through the automated insertion of the Guards into Binary code.
- Presentation Layer Modification:
By inserting malicious Java Script code into the binary code, presentation layer can be modified.
Check-Sum for Presentation Layer Check:
For the verification of presentation layer, perform a check sum. Match run-time check-sum result with the build time. Besides, observe that there are no unique binary signatures in both check sums.
- Cryptographic Key Replacement:
Data is stored in the encrypted and decrypted form over the server. Cyber attackers replace the cryptographic key to steal the data and sensitive information.
Use Dynamic Key:
In order to avoid the cryptographic key replacement, use dynamic key. In case of hard coded key, destroy the static key and while repairing the key, perform a check sum to verify that key is not tempered.
- Transport Layer Vulnerability:
Mobile devices are frequently vulnerable to Transport Layer attack. It directly relates how the mobile devices are connected to internet. When the mobile developer apply the Verification Security code once for both Wi-Fi and cellular mobile connection then the “MAN-IN-THE-MIDDLE” attacks arise which act as server for client and client for server and steal the Client-Server communication efficiently.
Secure TP Layer:
For mobile devices, there should be a strict implementation of the Security Certification and it should be done twice; one for mobile cellular device and other for Wi-Fi connections.
- Data Storage Insecure:
Mobile development focuses on the functionality of the apps rather than the security with limited resources. Poor focus on the secure data storage leads to the improper encryption of personal data like username, passwords, account numbers, personal details etc. Besides cloud backup storage also raise big concerns about the storage of data in secure form.
Focus on Proper Encryption and Decryption:
To secure the data storage, proper encryption and decryption is required with dedicated resources. Data storage security should be treated as high priority before the functionality of mobile apps.
- Session Handling:
Session handling is a big security concern for mobile applications. Many developers allow non- expiry long sessions or use sessions tokens which are predictable. Through improper session handling, cyber criminals illegally access the data through session hijacking.
Security of Session Handling:
Session should be non-expiry or there should be re-authentication of the session tokens.
References:
http://www.corero.com/blog/329-web-application-vulnerability-statistics-report-released.html
http://www.pcworld.com/article/262017/mobile_security_threats_rise.html
https://www.arxan.com/assets/1/7/State_of_Mobile_App_Security_2014_final.pdf











