Top Security Threats to Web Applications
- September 24, 2013
- admin
There are a number of security threats to web applications. Data centers and other assets which are used for hosting the websites should be protected from all types of threats. Threats must be identified by using application threat modeling and then must be evaluated with some vulnerability assessment.
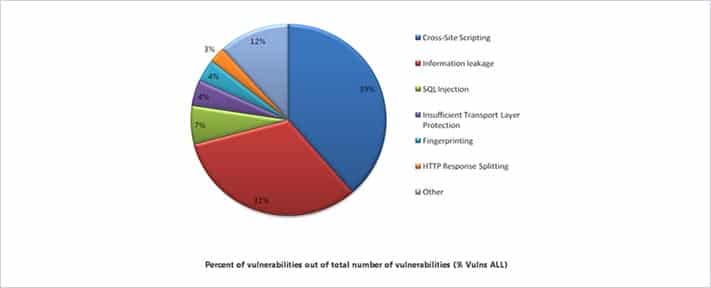
Brief descriptions of three major types of attacks are as follows:
SQL Injection:
SQL Injection (SQLI) is a code injection technique that exploits the database security vulnerabilities. The vulnerability is present when there are a few or no checks available for the user inputs for entering data in different types of data input fields. The user input may be a form of SQL query to exploit the vulnerability.
Cross Site Request Forgery:
Cross-site Request Forgery (CSRF) is a type of malicious attack whereby a trusted user of the website transmits unauthorized command. Unlike the Cross-site Scripting (XSS), which exploits the trust that a user has for some particular site, CSRF exploits the trust that a site has in a user’s browser.
Information Leakage:
Information Leakage takes place when a system which is designed to be closed to an eavesdropper(s) reveals some or all the information to the unauthorized parties.
Definitions of SQL Injection and Cross Site Scripting are described and it is the responsibility of the developers to control them, while the Information Leakage should be controlled by the management of the organization.
Besides these above mentioned top threats, there are also a number of security threats to the web applications including the Server Side Attacks, Client Side Attacks and some other advance type attacks. Some of these attacks are as follows:
Server Side Attacks
- SQL Injections
- LDAP Injections
- XPATH Injection
- OS Commanding
Client Side Attacks
- Cross Site Scripting
- CSRF
- Click Jacking
Advance Attacks
- Command Execution through Web Applications
- Source Code Disclosure
- DoS – Denial-of-Service
- Integer Overflow
- Remote File Include
- Open Redirect
Basic Attack Vectors
- Mapping assets to attacks
- Sifting through HTML source
- Forcing application layer errors
- Information leakage through error messages
- Brute forcing HTTP authentication
- Brute forcing HTML form authentication
Nowadays websites have become the number one target of choice of hackers’ attacks. Now, instead of attacking well defended network layers they prefer to attack more accessible web app layers which people use on daily basis to make transactions so that they can steal their credit card numbers and other private and confidential information. Therefore, it is essential to first successfully identify the kind of threat the website is facing and then deal with it using the right kind of techniques and tools.